ZeusTracker and the Nuclear Option
Brian Krebs, who blogs for the Washington Post in his "Security Fix" columns writes about the Zeus Tracker, a botnet which recently was responsible for flicking the "kill switch" on 100,000 PC's. Here's an excerpt from his article:
"One of the scarier realities about malicious software is that these programs leave ultimate control over victim machines in the hands of the attacker, who could simply decide to order all of the infected machines to self-destruct.
Most security experts will tell you that while this so-called "nuclear option" is an available feature in some malware, it is hardly ever used. Disabling infected systems is counterproductive for attackers, who generally focus on hoovering as much personal and financial data as they can from the PCs they control.
But try telling that to Roman Hüssy, a 21-year-old Swiss information technology expert, who last month witnessed a collection of more than 100,000 hacked Microsoft Windows systems tearing themselves apart at the command of their cyber criminal overlords.
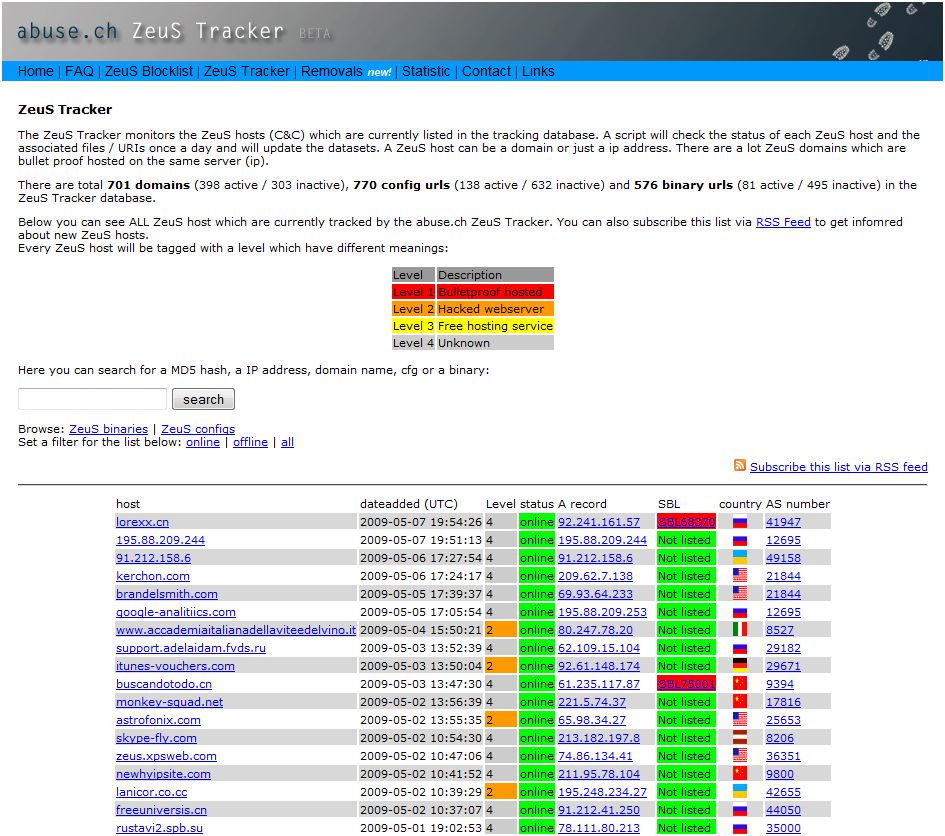
Hüssy oversees Zeustracker, a Web site listing Internet servers that use Zeus, a kit sold for about $700 on shadowy cyber criminal forums to harvest data from computers infected with a password stealing Trojan horse program. One of Zeus's distinguishing features is a tool that helps each installation on a victim PC look radically different from the next as a means to evade detection by anti-virus tools.
According to Hüssy, among Zeus's many features is the "kos" option, which stands for "kill operating system." The help file distributed with Zeus kits includes the following Google-translated explanation of this feature:kos - incapacitate OS, namely grip branches HKEY_CURRENT_USER registry and / or HKEY_LOCAL_MACHINE. If you have sufficient privileges - fly to "blue screen", in other cases creates the brakes. Following these steps, loading OS will not be possible!In early April, Hüssy began tracking a Zeus control server used to receive data stolen from a botnet of more than 100,000 infected systems, mostly located in Poland and Spain. While investigating this newfound Zeus control server, he noticed something unusual: the "kill operating system" had just been issued to all 100,000 infected systems.
Hüssy said he has no idea why the botnet was destroyed.
"Maybe the botnet was hijacked by another crime group," he offered in an online chat with Security Fix. Then again, maybe the individuals in control over that ill-fated botnet simply didn't understand what they were doing. "Many cyber criminals...using the Zeus crimeware kit aren't very skilled," Hüssy said.
Researchers at the S21sec blog have their own theory: that maybe attackers wield the nuclear option to buy themselves more time to use the stolen data.
"The point more probably for a phisher is to earn time," writes S21's Jozef Gegeny. "Taking the victim away from Internet connection - before the unwanted money transfer is realized and further actions could be taken."
As one might imagine, bad guys who control these Zeus crimeware servers aren't always too happy about having their networks called out. Since my interview with Hüssy on Wednesday, his site has come under a fairly massive distributed denial of service (DDoS) attack, no doubt from systems under the control of Zeus botmasters. "
Continue Reading at Brian Krebs Security Fix on the Washington Post





 According to
According to 

 Linkbee.com Adds Twitter Photo Sharing
Linkbee.com Adds Twitter Photo Sharing This is really a desperate act. Both Visa and MasterCard have already stated that Bobo's (Bob O.Carr) Heartland Payment Systems was NOT PCI compliant when the breach occurred and Bobo waited until he could unload a bunch of stock before he announced the breach under the cover of BO's inauguration. From Finextra:
This is really a desperate act. Both Visa and MasterCard have already stated that Bobo's (Bob O.Carr) Heartland Payment Systems was NOT PCI compliant when the breach occurred and Bobo waited until he could unload a bunch of stock before he announced the breach under the cover of BO's inauguration. From Finextra: 



 Bank Technology News contributor, John Adams, writes that Heartland is still reeling from the left hook thrown by Hackers:
Bank Technology News contributor, John Adams, writes that Heartland is still reeling from the left hook thrown by Hackers:
